Add unified communications on top of your existing voice services.
Connect Bria with any SIP-supported call servers or VoIP providers.
Bria is your interface for business-class communications
Access your lines of communications no matter anywhere you are.
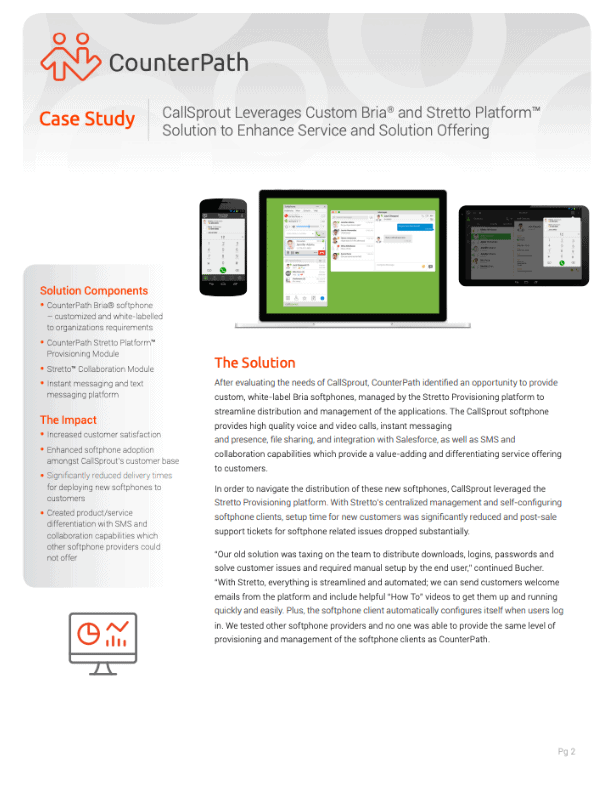
Softphone
Call with advanced call features - call transfer, forward and more.
Cloud Provisioning
Configure only once in the cloud and have settings downloaded into your device.
Team Messaging
Team messaging in a single window. Start 1:1 messages or chat rooms.
Management Tools
Access call analytics and help desk tools to administer your everyday operations.
Secure Communications
Encrypted voice and messaging keeps your communications private.
Any Device
From desktop to mobile devices, Bria lets you take your communications anywhere.

Develop or customize Bria
Every business communicates differently – Bria respects this, providing tailored solutions that streamline your communication and collaboration experience.
``We pride ourselves on delivering top of the line services and solutions, and our existing softphones just weren’t cutting it. We needed a solution that would be dependable and easy to manage and provide a consistent user experience. CounterPath delivered it all.``
Eric Bucher
CEO
See how Bria modernizes communications
Start Communicating with Bria
Download and try Bria for free! No credit card information required.





















